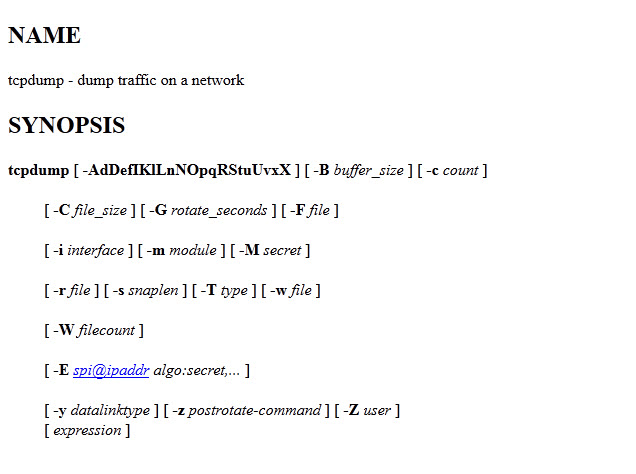
tcpdump is a command line network sniffer, used to capture network packets. When you have only command line terminal access of your system, this tool is very helpful to sniff network packets. It has so many options:
- you can see the packet dump in your terminal,
- you can also create a pcap file (to see the capture in wireshark),
- you can create filter to capture only required packets like ftp or ssh etc.
- you can directly see the capture of a remote system in any other Linux system using wireshark, for more detail click “Remote packet capture using WireShark and tcpdump”.
- so many other options available, see tcpdump man page.
tcpdump man page
When you create a pcap file using tcpdump it will truncate your capture file to shorten it and you may not able to understand that. I am writing this post, so that you can create a pcap file effectively. You can use following command to capture the dump in a file:
tcpdump -s 0 port ftp or ssh -i eth0 -w mycap.pcap
In above command
-s 0 will set the capture byte to its maximum i.e. 65535, after this capture file will not truncate.
-i eth0 is using to give Ethernet interface, which you to capture. Default is eth0, if you not use this option.
port ftp or ssh is the filter, which will capture only ftp and ssh packets. You can remove this to capture all packets.
-w mypcap.pcap will create that pcap file, which will be opened using wireshark.
wireshark.org
Now I think, you can play with the command as per your need.



Pingback: How to convert Tcpdump output file to a Pcap format?
good and simple howto! thanks!
Your welcome, thanks for coming :)
Thanks that was simple and works well.
Thanks for your feedback :-)
i still cannot open .pcap file in wireshark, can you help me?
Is this possible? Local -> ras1 ssh -> device ssh (tcpdump to pcap) and view the pcap file on the local host? I’m unable to ssh to the second connection without going to the first ras.
greetins to make tcupdump
why not to use wireshark direcly to make these dump
wireshark in linux is hard.
It can be used if available :-). But if you have only command line access without wireshark-gnome applet, tcpdump is a good option to make pcap dump.
Short and effective – also in 2017
Thanks for this
Thank you, please keep visiting.
Great.. as other said.. Short clear and helpful info..