As I wrote in my earlier post, I configured the L2TP tunnel using xl2tpd & rp-l2tpd application. But the primary application “xl2tpd” has a lot of bugs & I was frustrated of its problems. Finally I use rp-l2tpd only to make the L2TP VPN server. Thanks for project administrator of this application, It is almost a bug free L2TP VPN application & also very easy to configure (especially for my case).
Kernel Requirement of rp-l2tpd
ppp_generic: kernel config –> Network device support –> PPP (point-to-point protocol) support
ppp_synctty: kernel config –> Network device support –> PPP support for sync tty ports
slhc(optional): kernel config –> Network device support –> SLIP (serial line) support –> CSLIP compressed headers
n_hdlc: kernel config –> Character devices –> Non-standard serial port support –> HDLC line discipline support
Use the modprobe command to install the above modules:
modprobe ppp_generic
modprobe ppp_synctty
modprobe n_hdlc
If modules not able to load in your system, recompile & install your kernel with those modules.
To load those modules at startup, add above commands at /etc/rc.local or see this link http://www.centos.org/modules/newbb/viewtopic.php?topic_id=15303&forum=37&post_id=53665 if you are using CentOS.
Prepare the rp-l2tpd Server
To configure the rp-l2tpd VPN server, we need a Linux system with least of two network interfaces. I use Centos 5 Linux operating system for my VPN installation. You can also use other Linux’s flavors, but avoid using Fedora Core 8. Fedora Core 8 has some bug in pppd that doesn’t accept the connection from client.
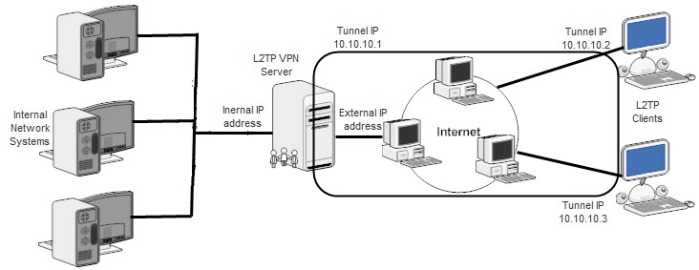
Activate the IP forwarding on the server to send the data of one to interface to other (from ppp tunnel interface to internal LAN interface). Use the following command to activate the IP forwarding.
| echo 1 > /proc/sys/net/ipv4/ip_forward |
Downloading & Installing rp-l2tpd
You can download rp-l2tpd from http://sourceforge.net/projects/rp-l2tp/. For installation follow the simple procedure.
| ./configuremakemake install |
rp-l2tpd Server Configuration
To configure the rp-l2tpd server, you need to change the following files.
/etc/l2tp/l2tp.conf
/etc/ppp/options
/etc/ppp/chap-secrets
l2tp.conf
This file has the configuration of L2TP server parameters.
| # Global section (by default, we start in global mode)global# Load handlersload-handler sync-pppd.soload-handler cmd.so# Bind address
listen-port 1701 # Configure the sync-pppd handler. You MUST have a “section sync-pppd” line # even if you don’t set any options. section sync-pppd # Configure the CHAP for ppp authentication, you can also use require-pap, but avoid this. lns-pppd-opts “require-chap 10.10.10.1: lcp-echo-interval 30 lcp-echo-failure 6” # Peer section section peer # For any peer enters the value 0.0.0.0 with mask 0, otherwise specify the static IP address of peer. peer 0.0.0.0 mask 0 port 1701 lac-handler sync-pppd lns-handler sync-pppd hide-avps yes # Configure the cmd handler. You MUST have a “section cmd” line # even if you don’t set any options. section cmd |
I don’t know how we can use mschap-v2 in this configuration file, if anyone knows please reply.
options
/etc/ppp/options file use to configure the pppd options.
| ipcp-accept-localipcp-accept-remotems-dns 10.10.10.254ms-wins 10.10.10.254noccpauth
crtscts idle 1800 mtu 1600 mru 1410 defaultroute debug lock proxyarp connect-delay 5000 |
Please look at the man page of pppd for detail on this file.
chap-secrets
Put your authentication on /etc/ppp/chap-secrets file.
| # Secrets for authentication using CHAP# client server secret IP addresses”username” “*” “password” “10.10.10.2” |
The IP address field is showing the remote tunnel static IP address. You can assign the dynamic IP addresses also by using radius server & dhcp-pppd plugin etc. Same chap-secrets file can be used, if you are using mschap protocol in option file.
Running rp-l2tpd
That’s all from the server configuration side, now you can start the rp-l2tpd server, use the following command.
| l2tpd -f -d 65535 |
“-f” is used to run l2tpd in foreground & “-d 65535” is used to open the debugs at highest level.
rp-l2tpd Client Configuration
The only change in the client configuration is in l2tp.conf file. For client, it is something like this
| # Global section (by default, we start in global mode)global# Load handlersload-handler sync-pppd.soload-handler cmd.so# Bind address
listen-port 1701 # Configure the sync-pppd handler. You MUST have a “section sync-pppd” line # even if you don’t set any options. section sync-pppd lac-pppd-opts “user nameofuser noipdefault ipcp-accept-local ipcp-accept-remote lcp-echo-interval 30 lcp-echo-failure 6” # Peer section to connect with server section peer # Replace 51.52.53.54 with your VPN server IP address peer 51.52.53.54 port 1701 lac-handler sync-pppd hide-avps no # Configure the cmd handler. You MUST have a “section cmd” line # even if you don’t set any options. section cmd |
In case of option file use the following entries only.
| lock noauth |
The user name i.e. used in the l2tp.conf file must enter in client’s chap-secrets file.
# Secrets for authentication using CHAP
# client server secret IP addresses
“username” “*” “password” “*”
Running L2TP Client
To run the rp-l2tpd client, first start the l2tpd service.
| l2tpd -f -d 65535 |
Then set up the connection with your L2TP VPN server by using following command.
| l2tp-control “start-session 51.52.53.54” |
If you give the ifconfig command it will show you a ppp0 connection when l2tp is connected.
Stopping L2TP Client
Use the following command to stop the L2TP client session.
| l2tp-control stop-session “your-Tunnel-ID your-Session-LAC-ID” |
To check what is your Tunnel-ID & Session-LAC-ID, use the following command.
| l2tp-control “dump-sessions” |
To stop all the connected sessions, use following command.
| l2tp-control “exit” |
Pingback: L2TP VPN using rp-l2tpd « Linux Explore
It is useful to try everything in practice anyway and I like that here it’s always possible to find something new. :)
This post is updated, i found some typo mistakes & correct them. Now anyone can try this. It will work fine. :)
If you find any problem, please write a comment.
If you like it, must share it with others.
Thanks for visiting.
dear rahul
rp-l2tp will work on centos VPS? or only on dedicated server?
sriram
It will work on any CentOS system with atleast two Ethernet cards, one is for internal LAN & other is for Public WAN connectivity.
Best regards
Dear Rahul
I mean it will work on Virtual Private Server? i have IP Phone but it is only support standard L2TP protocol (without pre-shared key).can i use rp-l2tp for this purpose?
I also used rp-l2tpd for same purpose. :)
To connect the IP Phone which only support L2TP without psk.
You can also use this. Your IP phone may be in some other public network behind the NAT.
IP phone will connect the L2TP server to its public IP or domain name & get the IP address according to your configuration.
You must activate the ip_forwarding to L2TP server to forward the packets of external interface to internal interface.
Best Regards
Dear rahul
how many clients can login to server? morethan 200 clients possible?
best regards
sriram
Depend on your bandwidth & server capability. I think there is no restriction on rp-l2tpd.
Dear rahul
thanks for help i am appreciating you can i get your personal email?
best regards
sriram
Hi!
Do you know if its possible to have many peer addresses on the client side in the l2tp.conf?
section peer
peer 51.52.53.54 <<< specifying two or more ip addresses on that line and then run the command like "l2tp-control “start-session 1.1.1.1" and l2tp-control “start-session 2.2.2.2.″?.
Regards
Thomas
No, it is not possible with that. You can’t use multiple entries on client peer.
But why do you need multiple peer on client side?
Obtain and select some good points from you and it helps me to solve a problem, thanks.
– Henry
Pingback: 2010 in review « Linux Explore
good site
Hi, great article, helps me a lot. But I have one question: how can I make this to assign dynamic ip addresses to lacs? You have lns-pppd-opts ”require-chap 10.10.10.1: lcp-echo-interval 30 lcp-echo-failure 6″ and for me with this config it returns error on lac that no ip address assigned, to make it working I have to insert lns-pppd-opts ”require-chap 10.10.10.1:10.10.10.2 lcp-echo-interval 30 lcp-echo-failure 6″ so my lns is 10.10.10.1 and lac 10.10.10.2, but what happens when more lacs appear?
Hi,
Try to allocate the IP address through chap-secrets.
Best regards
Rahul Panwar
thx for replay, but chap-secret solution is not so good… You have written that its possible to configure this with dhcp, have You try this? e.g. in xl2tpd You can define ip pool for lacs and this is great, I think missing this in rp-l2tpd is big mistake
It can be done using pppoe-server with this. But i didn’t try it. pppoe-server will allocate the ip pool for ppp client & authentication will handled by pap/chap-secrets.
Best regards
Dear rahul
THIS VPN ALL ARE USING FOR ILLEGAL PURPOSE WHY YOU HELPING TO DO ILLEGAL? I HOPE U R GOOD MAN DON’T HELP FOR ILLEGAL
Hi Martin,
I don’t know who you are, why you are telling this?
I just write here “How to configure rp-l2tpd/xl2tpd”, you can also find so many other website like this. I don’t understand why you are stopping me to SHARE KNOWLEDGE of a LEGAL thing, because VPN is not ILLEGAL.
If you really think that this is ILLEGAL then stop the companies who are developing & doing paid support for this type of applications.
Sorry Mr Martin, i am just a supporter of OPEN source/Linux & not doing anything ILLEGAL here.
Thanks & Regards,
Rahul Panwar
Dear Rahul
I hope you are remembering one sriram did you help him? but he installed himself openL2TP for me. he is my technician now. i know you dont know more about l2tp so you skipped from his doubts that time you said cant help l2tp vpn is illegal. now you are saying not illegal are you not normal?
Ok, then talk to him, why are you talking to me?
Because i didn’t help him, i didn’t write here that “How to configure OpenL2TP” & “How can you use it ILLEGALLY”…..
Tell me, what do you really want from me????
this is ur words…..
Hi Sriram,
Sorry for late response.
Thanks for your appreciation.
now a day i am very busy with my projects.
I can’t help you on that? It is illegal.
Sorry for that but i can’t support you for an illegal work.
:) Is that mean i am doing illegal………..
This is your last,,,
Are you telling your real concern ????????? or i will block your comments?
I can see that you are putting a lots of efforts into your blog. Keep posting the good work.Some really helpful information in there. Bookmarked. Nice to see your site. Thanks! Regard
Hi
i have just downloaded rp-l2tpd
./configure works fine , but make does work it show me error :
make -C handlers
make[1]: entrant dans le répertoire « /home/fikri/Bureau/rp-l2tp-0.4/handlers »
make[1]: Rien à faire pour « all ».
make[1]: quittant le répertoire « /home/fikri/Bureau/rp-l2tp-0.4/handlers »
plz help me
hello i need help. I installed l2tp+ipsec with this automated script:
http://mirror.zeddicus.com/auto-l2tp/1.2/centos/l2tp.sh
it was easy and was done within 1 min, i didnt even have to configure the firewall!
however, it seems to crash randomly. It seems that when it crash, i cannot login to the vpn, and i have to manually do a “/etc/init.d/ipsec restart” to fix it. I also cannot find command to stop or start xl2tpd or xl2tp, im not sure what l2tp it is using can you help check it out for me?
i am not a pro here but desperately need help to fix the random “cannot login” problem
Hi
This website is very useful. thanks for help to everybody.i am followed your instructions and installed rp-l2tpd everything sccess. clients can sucessfully connect to server but one problem is client cant get internet from server.Please help me. thanks.
I just want to mention I am just very new to weblog and truly loved your web blog. Almost certainly I’m going to bookmark your website . You actually come with excellent well written articles. Bless you for sharing with us your website page.
I simply want to mention I am just new to blogs and seriously liked your web-site. More than likely I’m likely to bookmark your blog post . You really come with superb stories. Thanks a bunch for sharing with us your blog site.
This will be a fantastic blog, could you be involved in doing an interview about how you created it? If so e-mail me
Pingback: IPSec Communication for VPN Setup in CentOS 6 / RHEL 6.3 | Linux Explore
Hi, I have a virtual server running over KVM visualization and using CPanel, does the above solution interfere with CPanel knowing that the server is hosting 50+ website
Thanks for visiting my blog. I hope you like it. :-)
The interference depends on the network configuration done on the server.
With havin so much content do you ever run into any issues
of plagorism or copyright infringement? My site has a lot of unique content I’ve either authored myself or outsourced but it appears a lot of it is popping it up all over the internet without my agreement. Do you know any methods to help protect against content from being ripped off? I’d really appreciate it.
Hi ,
I tried 0.4 version of rp-l2tp for server setting but when I try to connect using Windows 7 or my Android phone then tunnel disconnections in few seconds…….here is log.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
700.256 dgram_take_from_wire() -> type=SCCRQ, tid=0, sid=0, Nr=0, Ns=0
700.256 tunnel_new() -> 50840/0
700.257 50840/0: Peer host name is ‘anonymous’
700.257 l2tp_peer_find(59.120.37.1) examining peer 0.0.0.0/0
700.257 l2tp_peer_find(59.120.37.1) found 0.0.0.0/0
700.257 tunnel(50840/47420) state idle -> wait-ctl-conn
700.257 tunnel_enqueue_dgram(50840/47420, SCCRP) rws=1 cwnd=1 ssthresh=1 outstanding=0
700.257 xmit_queued(50840/47420): rws=1 cwnd=1 ssthresh=1 outstanding=0
700.257 dgram_send_to_wire() -> type=SCCRP, tid=47420, sid=0, Nr=1, Ns=0
700.257 loop in xmit_queued(50840/47420): rws=1 cwnd=1 ssthresh=1 outstanding=1
700.286 dgram_take_from_wire() -> type=SCCCN, tid=50840, sid=0, Nr=1, Ns=1
700.286 tunnel_schedule_ack(50840/47420)
700.286 tunnel_dequeue_acked_packets(50840/47420) rws=1 cwnd=1 ssthresh=1 outstanding=0
700.286 tunnel_process_received_datagram(50840/47420, SCCCN)
700.286 tunnel(50840/47420) state wait-ctl-conn -> established
700.432 tunnel_do_ack(50840/47420)
700.440 dgram_send_to_wire() -> type=ZLB, tid=47420, sid=0, Nr=2, Ns=1
700.462 dgram_take_from_wire() -> type=ICRQ, tid=50840, sid=0, Nr=1, Ns=2
700.463 tunnel_schedule_ack(50840/47420)
700.463 tunnel_dequeue_acked_packets(50840/47420) rws=1 cwnd=1 ssthresh=1 outstanding=0
700.463 tunnel_process_received_datagram(50840/47420, ICRQ)
700.463 session((50840/47420, 65330/44922)) state idle -> wait-connect
700.463 tunnel_enqueue_dgram(50840/47420, ICRP) rws=1 cwnd=1 ssthresh=1 outstanding=0
700.463 xmit_queued(50840/47420): rws=1 cwnd=1 ssthresh=1 outstanding=0
700.463 dgram_send_to_wire() -> type=ICRP, tid=47420, sid=44922, Nr=3, Ns=1
700.463 loop in xmit_queued(50840/47420): rws=1 cwnd=1 ssthresh=1 outstanding=1
700.487 dgram_take_from_wire() -> type=ICCN, tid=50840, sid=65330, Nr=2, Ns=3
700.487 tunnel_schedule_ack(50840/47420)
700.487 tunnel_dequeue_acked_packets(50840/47420) rws=1 cwnd=1 ssthresh=1 outstanding=0
700.487 tunnel_process_received_datagram(50840/47420, ICCN)
700.487 session((50840/47420, 65330/44922)) state wait-connect -> established
700.609 tunnel_do_ack(50840/47420)
700.609 dgram_send_to_wire() -> type=ZLB, tid=47420, sid=0, Nr=4, Ns=2
700.682 session_send_CDN((50840/47420, 65330/44922)): pppd process exited
700.682 session((50840/47420, 65330/44922)) state established -> idle
700.682 tunnel_enqueue_dgram(50840/47420, CDN) rws=1 cwnd=1 ssthresh=1 outstanding=0
700.682 xmit_queued(50840/47420): rws=1 cwnd=1 ssthresh=1 outstanding=0
700.682 dgram_send_to_wire() -> type=CDN, tid=47420, sid=44922, Nr=4, Ns=2
700.683 loop in xmit_queued(50840/47420): rws=1 cwnd=1 ssthresh=1 outstanding=1
700.690 session_free((50840/47420, 65330/44922)) pppd process exited
700.690 tunnel_send_StopCCN(50840/47420, 1, 0, Last session has closed)
700.690 tunnel(50840/47420) state established -> sent-stop-ccn
700.691 tunnel_enqueue_dgram(50840/47420, StopCCN) rws=1 cwnd=1 ssthresh=1 outstanding=1
700.691 xmit_queued(50840/47420): rws=1 cwnd=1 ssthresh=1 outstanding=1
700.708 dgram_take_from_wire() -> type=StopCCN, tid=50840, sid=0, Nr=3, Ns=4
700.708 tunnel_schedule_ack(50840/47420)
700.708 tunnel_dequeue_acked_packets(50840/47420) rws=1 cwnd=1 ssthresh=1 outstanding=0
700.708 tunnel_process_received_datagram(50840/47420, StopCCN)
700.708 tunnel(50840/47420) state sent-stop-ccn -> received-stop-ccn
700.708 dgram_send_to_wire() -> type=ZLB, tid=47420, sid=0, Nr=5, Ns=3
700.708 tunnel_schedule_destruction(50840/47420)
731.740 tunnel_free(50840/47420)
746.089 dgram_take_from_wire() -> type=SCCRQ, tid=0, sid=0, Nr=0, Ns=0
746.089 tunnel_new() -> 60687/0
746.089 60687/0: Peer host name is ‘anonymous’
746.089 l2tp_peer_find(59.120.37.1) examining peer 0.0.0.0/0
746.089 l2tp_peer_find(59.120.37.1) found 0.0.0.0/0
746.089 tunnel(60687/34032) state idle -> wait-ctl-conn
746.089 tunnel_enqueue_dgram(60687/34032, SCCRP) rws=1 cwnd=1 ssthresh=1 outstanding=0
746.089 xmit_queued(60687/34032): rws=1 cwnd=1 ssthresh=1 outstanding=0
746.089 dgram_send_to_wire() -> type=SCCRP, tid=34032, sid=0, Nr=1, Ns=0
746.089 loop in xmit_queued(60687/34032): rws=1 cwnd=1 ssthresh=1 outstanding=1
746.120 dgram_take_from_wire() -> type=SCCCN, tid=60687, sid=0, Nr=1, Ns=1
746.120 tunnel_schedule_ack(60687/34032)
746.120 tunnel_dequeue_acked_packets(60687/34032) rws=1 cwnd=1 ssthresh=1 outstanding=0
746.120 tunnel_process_received_datagram(60687/34032, SCCCN)
746.120 tunnel(60687/34032) state wait-ctl-conn -> established
746.221 tunnel_do_ack(60687/34032)
746.221 dgram_send_to_wire() -> type=ZLB, tid=34032, sid=0, Nr=2, Ns=1
746.351 dgram_take_from_wire() -> type=ICRQ, tid=60687, sid=0, Nr=1, Ns=2
746.351 tunnel_schedule_ack(60687/34032)
746.351 tunnel_dequeue_acked_packets(60687/34032) rws=1 cwnd=1 ssthresh=1 outstanding=0
746.351 tunnel_process_received_datagram(60687/34032, ICRQ)
746.351 session((60687/34032, 54473/7786)) state idle -> wait-connect
746.351 tunnel_enqueue_dgram(60687/34032, ICRP) rws=1 cwnd=1 ssthresh=1 outstanding=0
746.351 xmit_queued(60687/34032): rws=1 cwnd=1 ssthresh=1 outstanding=0
746.351 dgram_send_to_wire() -> type=ICRP, tid=34032, sid=7786, Nr=3, Ns=1
746.352 loop in xmit_queued(60687/34032): rws=1 cwnd=1 ssthresh=1 outstanding=1
746.391 dgram_take_from_wire() -> type=ICCN, tid=60687, sid=54473, Nr=2, Ns=3
746.391 tunnel_schedule_ack(60687/34032)
746.391 tunnel_dequeue_acked_packets(60687/34032) rws=1 cwnd=1 ssthresh=1 outstanding=0
746.391 tunnel_process_received_datagram(60687/34032, ICCN)
746.391 session((60687/34032, 54473/7786)) state wait-connect -> established
746.536 tunnel_do_ack(60687/34032)
746.536 dgram_send_to_wire() -> type=ZLB, tid=34032, sid=0, Nr=4, Ns=2
746.539 session_send_CDN((60687/34032, 54473/7786)): pppd process exited
746.539 session((60687/34032, 54473/7786)) state established -> idle
746.539 tunnel_enqueue_dgram(60687/34032, CDN) rws=1 cwnd=1 ssthresh=1 outstanding=0
746.539 xmit_queued(60687/34032): rws=1 cwnd=1 ssthresh=1 outstanding=0
746.539 dgram_send_to_wire() -> type=CDN, tid=34032, sid=7786, Nr=4, Ns=2
746.540 loop in xmit_queued(60687/34032): rws=1 cwnd=1 ssthresh=1 outstanding=1
746.540 session_free((60687/34032, 54473/7786)) pppd process exited
746.540 tunnel_send_StopCCN(60687/34032, 1, 0, Last session has closed)
746.540 tunnel(60687/34032) state established -> sent-stop-ccn
746.540 tunnel_enqueue_dgram(60687/34032, StopCCN) rws=1 cwnd=1 ssthresh=1 outstanding=1
746.540 xmit_queued(60687/34032): rws=1 cwnd=1 ssthresh=1 outstanding=1
746.646 dgram_take_from_wire() -> type=StopCCN, tid=60687, sid=0, Nr=3, Ns=4
746.646 tunnel_schedule_ack(60687/34032)
746.646 tunnel_dequeue_acked_packets(60687/34032) rws=1 cwnd=1 ssthresh=1 outstanding=0
746.646 tunnel_process_received_datagram(60687/34032, StopCCN)
746.646 tunnel(60687/34032) state sent-stop-ccn -> received-stop-ccn
746.646 dgram_send_to_wire() -> type=ZLB, tid=34032, sid=0, Nr=5, Ns=3
746.646 tunnel_schedule_destruction(60687/34032)
777.678 tunnel_free(60687/34032)
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
from log I can get that tunnel is connected and then disconnect.
One question: is it needed to give static IP for l2tp client ?
but i find no way to set static IP for the tunnel on Windows 7 or Android phone, what that i can only set is server IP, user, password and secrets.
Any guess, whats going wrong.
Thanks in advance.
Pingback: Learn To Sing Xubuntu | Learning To Sing