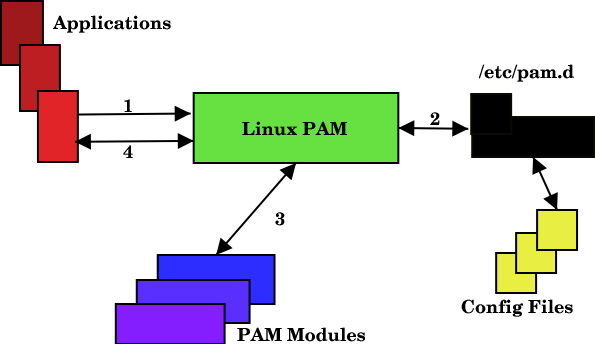
PAM Radius Module allows any PAM-capable machine to become a RADIUS client for authentication and accounting requests. The actual authentication will be performed by a RADIUS server. The freeradius can be used for radius server.
Download the PAM Radius Module
To download the PAM Radius module, click here.
Installing & configuring PAM Radius Module
To install PAM radius module, give the following commands:
[root@rahul-pc]# tar -xvf pam_radius-1.3.17.tar.gz
[root@rahul-pc]# cd pam_radius-1.3.17
[root@rahul-pc]# make
It will generate a library file pam_radius_login.so. Copy that file to /lib/security/ directory.
[root@rahul-pc]# cp pam_radius_login.so /lib/security/
Create a directory /etc/raddb/. Copy the file pam_radius_auth.conf to /etc/raddb/ directory named as server.
[root@rahul-pc]# mkdir /etc/raddb/
[root@rahul-pc]# cp pam_radius_auth.conf /etc/raddb/server
Change the file /etc/raddb/server according to your configuration.
# Radius Server IP address Secret Timeout
192.168.2.43 yoursecret 3
Configure PAM Applications for Radius Server
After doing the above configurations, edit the PAM application’s files to authenticate from radius server.
SSH server configuration
To authenticate the SSH server request from radius server, edit the file /etc/pam.d/sshd. Add a new line
auth sufficient pam_radius_auth.so
above the following line
auth include system-auth
After changing the PAM file, the authentication request for SSH server will go to the configured radius server (192.168.2.43 in our example) first. If the request is not accepted from radius server, then it will check the system-authentication.
Password change configuration
Similarly, to change the password of any SSH user, change the file /etc/pam.d/passwd. Add a new line
password sufficient pam_radius_auth.so
above the following line
password include system-auth
After this password change request will go to the radius server.
FTP Server Configuration
Similarly do the above changes for vsftpd file in /etc/pam.d/ directory. Then the entire authentication request for FTP server will go to radius server.
In the same way do the changes for other required applications.

Generally I do not read post on blogs, however I wish to say that this write-up very forced me to take a look at and do it! Your writing taste has been amazed me. Thanks, quite nice post.
Does this require a home directory for each user to reside on the physical SSH server? I am hoping to find a solution that will allow SSH authentication via radius with just the username/password credentials stored in radius and not have to create a home directory for each user. Also, does the user need to exist in etc/passwd ? Nice article.
Please Did you get any information on this, pls pass om
Does this method require a local user account on the SSH server itself or does it rely completely on the user account information that resides on the Radius server? I see other posts that mention a requirement to have a local account (i.e. home directory and/or listed in etc/passwd). I am hoping your post shows a method that does not require anything local on the SSH server itself. Nice article!
same process followed but getting alot of issue with the compilation
Please post the errors log.
Hi, nice writeup, I want to know if this configuration will work with windows radius server (NPS) or not.
I didn’t check with windows, but it follows radius protocol. So it might work.
Why don’t you check and reply back, if you have windows radius server. :-)
I downloaded pam_radius-1.4.0.tar.gz, and after unzipping I am running make command but it is giving me lots of below mentioned errors, I am trying this on RHEL6.4.
#make
cc -Wall -fPIC -c src/pam_radius_auth.c -o pam_radius_auth.o
In file included from src/pam_radius_auth.c:62:
src/pam_radius_auth.h:4:20: error: config.h: No such file or directory
src/pam_radius_auth.h:35:4: error: #error security/pam_modules.h or pam/pam_modules.h required
src/pam_radius_auth.c:183: error: expected â)â before â*â token
src/pam_radius_auth.c: In function âhost2serverâ:
src/pam_radius_auth.c:294: error: âPAM_AUTHINFO_UNAVAILâ undeclared (first use in this function)
src/pam_radius_auth.c:294: error: (Each undeclared identifier is reported only once
src/pam_radius_auth.c:294: error: for each function it appears in.)
src/pam_radius_auth.c:336: error: âPAM_SUCCESSâ undeclared (first use in this function)
src/pam_radius_auth.c: In function âinitializeâ:
src/pam_radius_auth.c:613: error: âPAM_ABORTâ undeclared (first use in this function)
src/pam_radius_auth.c:670: error: âPAM_AUTHINFO_UNAVAILâ undeclared (first use in this function)
src/pam_radius_auth.c:694: error: âPAM_SUCCESSâ undeclared (first use in this function)
src/pam_radius_auth.c: In function âtalk_radiusâ:
Problem is coming with the “config.h” file, which might not exist. You are using latest version (pam_radius-1.4.0.tar.gz), which need to be configured first. Did you execute the ./configure script before start compiling?
Please use following steps:
1. extract the source.
2. goto to source directory.
3. ./configure
4. make
That might help.
Hi Rahul,
Thanks, after installing pam_modules.h, it worked :-) , I have configured the radius PAM module and added my linux server as radius client in windows NPS server, but somehow authentication is not working.
I dont see any traffic on NPS server coming from linux client, also in /var/log/secure, it is showing myuser as unknown, and below errors.
Jul 4 09:01:02 mylinux sshd[2278]: pam_radius_auth: Got user name linuxuser
Jul 4 09:01:02 mylinux sshd[2278]: pam_radius_auth: ignore last_pass, force_prompt set
Jul 4 09:01:02 mylinux sshd[2278]: pam_radius_auth: Sending RADIUS request code 1
Jul 4 09:01:02 mylinux sshd[2278]: pam_radius_auth: DEBUG: getservbyname(radius, udp) returned 0x7fdcfa64f980.
Jul 4 09:01:02 mylinux sshd[2278]: pam_radius_auth: Got RADIUS response code 3
Jul 4 09:01:02 mylinux sshd[2278]: pam_radius_auth: authentication failed
The response code 3 stands for Access reject.
Can you please guide me how can I find the issue.
Good it know it helps.
Look like Your radius server is receiving the authentication request but it is rejecting. Did you create your Linux user into radius server?
Thanks, you are right, user is in windows active directory, I checked the NPS logs, it is giving reason code 16, which means wrong username or password, I am checking the NPS configuration.
MyLinuxRadiusClientNameInNPS
3
16
I am glad, you found it.
Please keep visiting for latest updates. And you know sharing is caring ;-) so keep sharing also.
You might wanna join me on twitter and Facebook.
Hi Rahul,
I follow the above steps on my Centos bur not able see any messages in /var/log/secure, can you please help in how to enable debug log to see those messages